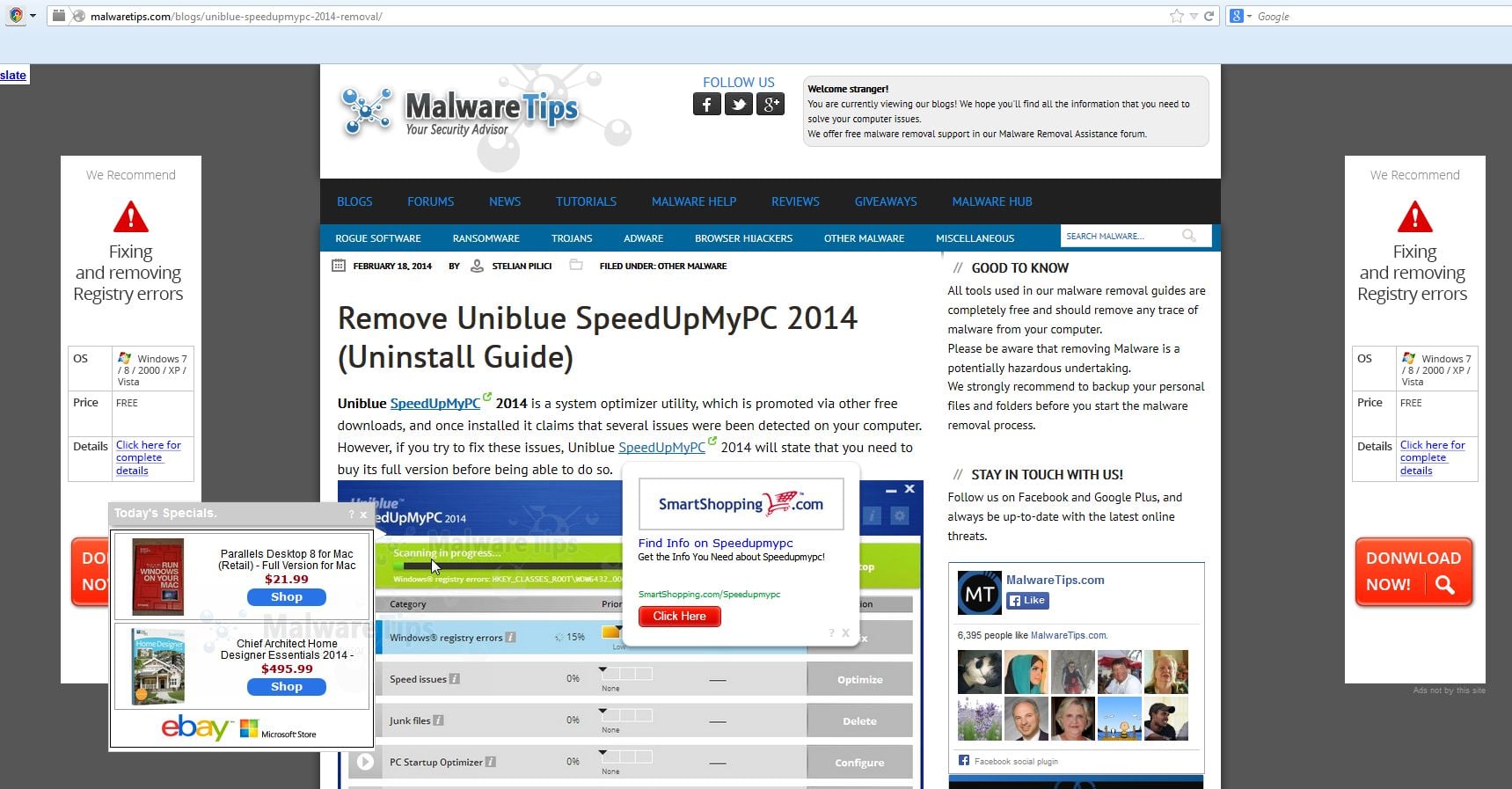
According to security researchers, PromoteMethod is an adware program. How does adware work? Adware is form of malicious software which displays unwanted ads on a machine, redirects search requests to advertising web sites and gathers confidential data for marketing purposes. Adware can show banner advertisements, full-screen advertisements, pop ups, videos, or other varieties of online advertising. Adware can attack your computer’s browsers such as the Firefox, Safari and Google Chrome. Maybe you approve the idea that the advertisements or popups is just a small problem. But these intrusive ads eat MAC OS resources and slow down your MAC system performance.
Protect your Mac from malware. MacOS has many features that help protect your Mac and your personal information from malicious software, or malware. One common way malware is distributed is by embedding it in a harmless-looking app. You can reduce this risk by using software. Apr 12, 2020 Malwarebytes Anti-Malware for Mac. Windows users have long turned to Malwarebytes’ free version as a backup for always-on malware software. The Mac version started as an adware. Jun 09, 2020 Webroot: Webroot's antivirus software packages start at $29.99/$39.99 for one year and a single device with basic malware protections and a few extras.At the high end, these plans cost up.
Does adware steal your data? The PromoteMethod adware can collect lots of marketing-type data about you such as what web-pages you are opening, what you are looking for the Internet and so on. This personal info, later, may be sold to third parties.
How does PromoteMethod get on your computer
Most of undesired advertisements and pop ups come from web-browser toolbars and/or addons, and third-party applications. Most commonly, these items claim itself as software that improve your experience on the Internet by providing a fast and interactive start page or a search provider that does not track you. Remember, how to avoid the unwanted software. Be cautious, start only reputable apps which download from reputable sources. NEVER install any unknown and questionable programs.
Threat Summary
| Name | PromoteMethod, Promote Method 1.0 app |
| Type | adware software, PUP (potentially unwanted program), pop up virus, pop ups, pop up advertisements |
| Symptoms |
|
| Removal | PromoteMethod removal guide |
Remove PromoteMethod adware
When the adware gets installed on your MAC system without your knowledge, it is not easy to uninstall. In most cases, there is no Uninstall application which simply remove the PromoteMethod adware software from your Apple Mac. So, we suggest using well-proven free specialized tool such as MalwareBytes Anti-Malware (MBAM). But the best solution to get rid of PromoteMethod will be to perform several manual steps, after that additionally use antimalware tools.
To remove PromoteMethod, complete the following steps:
- How to manually remove PromoteMethod
- Automatic Removal of PromoteMethod adware software
How to manually remove PromoteMethod
First try to delete PromoteMethod manually; to do this, follow the steps below. Of course, manual adware removal requires more time and may not be suitable for those who are poorly versed in system settings. In this case, we suggest that you scroll down to the section that describes how to get rid of PromoteMethod adware using free tools.
Uninstall PUPs through the Finder
First method for manual adware removal is to go into the Finder, then Applications. Take a look at the list of applications on your computer and see if there are any questionable and unknown apps. If you see any, you need to delete them. Of course, before doing so, you can do an Internet search to find details on the application. If it is a potentially unwanted program, adware software or malicious software, you will likely find information that says so.
Open Finder and click “Applications”.
It will open a list of all applications installed on your Apple Mac. Scroll through the all list, and remove any dubious and unknown applications. Right click to suspicious application and select “Move to Trash”. Another solution is drag the program from the Applications folder to the Trash.
Most important, scroll through the all list, and move to trash any unknown applications. Don’t forget, choose Finder -> Empty Trash.
Remove PromoteMethod adware from Safari
If you find that Safari web browser settings such as new tab, startpage and search provider having been modified by PromoteMethod adware, then you may revert back your settings, via the reset web browser procedure.
Run Safari web browser. Next, select Preferences from the Safari menu.
First, click the “Security” icon. Here, choose “Block pop-up windows”. It will stop some types of pop-ups.
Now, click the “Extensions” icon. Look for dubious add-ons on left panel, choose it, then press the “Uninstall” button. Most important to get rid of all questionable addons from Safari.
Once complete, check your startpage and search engine settings. Click “General” icon. Make sure that the “Homepage” field contains the website you want or is empty.
Make sure that the “Search engine” setting shows your preferred search engine. In some versions of Safari, this setting is in the “Search” tab.
Remove PromoteMethod from Google Chrome
Annoying PromoteMethod ads or other symptom of having adware software in your browser is a good reason to reset Google Chrome. This is an easy method to restore the Google Chrome settings and not lose any important information.
- First launch the Google Chrome and click Menu button (small button in the form of three dots).
- It will display the Chrome main menu. Choose More Tools, then click Extensions.
- You’ll see the list of installed add-ons. If the list has the plugin labeled with “Installed by enterprise policy” or “Installed by your administrator”, then complete the following guide: Remove Chrome extensions installed by enterprise policy.
- Now open the Google Chrome menu once again, press the “Settings” menu.
- You will see the Google Chrome’s settings page. Scroll down and click “Advanced” link.
- Scroll down again and click the “Reset” button.
- The Google Chrome will display the reset profile settings page as shown on the screen above.
- Next press the “Reset” button.
- Once this process is done, your web browser’s search provider, startpage and newtab page will be restored to their original defaults.
- To learn more, read the post How to reset Chrome settings to default.
Remove PromoteMethod adware from Firefox
The Firefox reset will remove PromoteMethod ads, modified preferences, extensions and security settings. It’ll keep your personal information like browsing history, bookmarks, passwords and web form auto-fill data.
First, run the Firefox. Next, press the button in the form of three horizontal stripes (). It will open the drop-down menu. Next, press the Help button ().
In the Help menu press the “Troubleshooting Information”. In the upper-right corner of the “Troubleshooting Information” page click on “Refresh Firefox” button as shown in the following example.
Confirm your action, click the “Refresh Firefox”.
Automatic Removal of PromoteMethod adware software
Adware Removal For Mac
Spyware, adware, PUPs and hijackers can be difficult to get rid of manually. Do not try to remove this software without the help of malicious software removal utilities. In order to completely remove adware from your computer, run professionally created utility such as MalwareBytes.
Run MalwareBytes Anti-Malware (MBAM) to remove PromoteMethod adware
Manual PromoteMethod removal requires some computer skills. Some files that created by the adware may be not completely removed. We recommend that run the MalwareBytes that are completely free your MAC of adware. Moreover, this free utility will allow you to delete hijacker, malicious software, potentially unwanted software and toolbars that your machine can be infected too.
- MalwareBytes can be downloaded from the following link.Malwarebytes Anti-malware (Mac)
14185 downloads
Author: Malwarebytes
Category: Security tools
Update: July 10, 2018 - Once the downloading process is finished, please close all apps and open windows on your computer. Run the downloaded file. Follow the prompts.
- The MalwareBytes AntiMalware (MBAM) will open and show the main window.
- Further, click the “Scan” button to scan for PromoteMethod adware. A scan may take anywhere from 10 to 30 minutes, depending on the number of files on your computer and the speed of your Apple Mac. While the MalwareBytes Free is scanning, you can see how many objects it has identified either as being malicious software.
- When the checking is complete, you may check all threats detected on your MAC system.
- Review the results once the tool has done the system scan. If you think an entry should not be quarantined, then uncheck it. Otherwise, simply press the “Remove Selected Items” button.
- Close the Anti-Malware and continue with the next step.
How to stay safe online
The AdGuard is a very good ad blocker application for the Safari, Google Chrome and Mozilla Firefox, with active user support. It does a great job by removing certain types of unwanted ads, popunders, pop-ups, annoying newtab pages, and even full page ads and webpage overlay layers. Of course, the AdGuard can stop unwanted web-sites automatically or by using a custom filter rule.
Installing the AdGuard is simple. First you’ll need to download AdGuard on your MAC OS from the link below.
2564 downloads
Author: © Adguard
Category: Security tools
Update: January 17, 2018
When downloading is finished, run the downloaded file. The “Setup Wizard” window will show up on the computer screen.
Follow the prompts. AdGuard will then be installed. A window will show up asking you to confirm that you want to see a quick tutorial. Press “Skip” button to close the window and use the default settings, or click “Get Started” to see an quick tutorial that will help you get to know AdGuard better.
Each time, when you start your computer, AdGuard will launch automatically and stop intrusive pop up ads, block harmful and misleading web sites.
To sum up
Now your machine should be clean of the PromoteMethod adware. We suggest that you keep MalwareBytes Free (to periodically scan your MAC system for new adwares and other malicious software) and AdGuard (to help you block undesired ads and malicious webpages). Moreover, to prevent any adware software, please stay clear of unknown and third party programs.
If you need more help with PromoteMethod related issues, go to here.
(1 votes, average: 5.00 out of 5)Loading...
For the past few years, adware has been one of the biggest cybersecurity threats in the digital world. In fact, it became much more aggressive last year, heavily targeting businesses and consumers using Windows, Mac, and Android devices. There were around 24 million Windows adware detections and 30 million Mac detections, according to Malwarebytes’ report.
What makes adware so widespread is that users don’t actually consider it as harmful as the other types of malware. And most of those whose computers have been infected are actually not aware of the presence of adware. When they see a lot of ads on their browsers, they just shrug them off as ads being displayed by the website they are visiting.
Unfortunately, most people are actually underestimating the consequences of being infected by adware. Adware, by itself, may not be as dangerous as other malware, like Trojans and ransomware. However, its danger lies in its ability to redirect the affected users to potentially dangerous websites.
One of the most popular adware right now is Turbostream, a browser redirect that tricks users into subscribing to its push notifications to be able to deliver unwanted and annoying advertising on the affected computer. It basically works just like other malware, but this adware uses multiple domains to proliferate the malicious software.
If you think your device or computer has been infected by the Turbostream malware, this article should help you understand what this adware does to your system and how it got in in the first place. We’ll also show you the step-by-step Turbostream removal instructions.
What is Turbostream?
Turbostream is adware distributed by malicious pop-up notifications that try to scam users into subscribing to its push notifications so that the adware can deliver unwanted advertisements straight to the victim’s computer. These notifications appear when you visit any of the Turbostream designed for the distribution of the malware. Here are some of the URLs where the Turbostream pop-ups can be found:
- Turbostream.club
- Turbostream.bar
- Turbostream.icu
- Turbostream.fun
- Videostay.site
- Videostay.uno
- Antihipe.club
As the website name suggests, these websites pose as fake streaming websites to lure users who want to access free movies. When you visit any of these websites, a message will immediately pop up, asking you to subscribe to all notifications from the website. It may look harmless, since a lot of websites do this to make it easier for users to be notified of new content or the latest updates on the website, but this Turbostream notification message functions differently from other websites’ notifications.
Here is the pop-up message that you will usually encounter:
Turbostream.club wants to Show notifications
Please Press Allow to Continue Watch!
The message is the same for all the URLs listed above. If you click the Allow button, you will eventually be bombarded by unwanted pop-up advertisements from Turbostream on your browser, even when you’re no longer on that website or sometimes, even when the browser is closed.

Clicking the Allow button will give the adware opportunity to install itself on your computer, add an extension to your browser, modify your browser settings, and spam your web browser with unwanted ads. You will also need to manually remove the permission you granted.
This Turbostream adware is composed of a network of rogue websites that works in the same way as many other adware-type malware and sites. When you check out the URLs listed above, you’ll find that there really isn’t any useful content on the website. You’ll only see a black square that looks like a media player before everything is grayed out and the notification pops up. Click the Allow button won’t load any real content from the website. Instead, you’ll be redirected to other websites where annoying ads are hosted. Clicking the Block button will also result in the same result. This means that the adware download will be triggered no matter what button you click. As long as you click anywhere in the pop-up message, the malware will be downloaded to your website nonetheless.
The Turbostream website was only created to trigger notification subscription forms, as well as enable additional material from sponsored pages and other advertisers. These websites all are managed by PUP developers and advertisers, and they are usually designed in the same way as Pushtoday.icu, Nextyourcontent.com, Solo84.biz, Eztv.io, and utorrentie.exe.
Turbostream is designed based on social engineering techniques, so pop-ups, notifications, ads, and other content shown by this adware can also trigger various types of additional content. Turbostream is not actually a vicious malware because all it does is display ads. But aside from the annoying redirects that repeat over and over again, visiting these websites can also expose your device to more harmful malware.
How Is Turbostream Being Distributed?
The most common methods of malware distribution is through deceptive website advertisements. You might have clicked on an ad somewhere that promotes the Turbostream website, redirecting you to the malicious website. Most of these ads are sponsored and targeted. Once you click the ad, you will be sent to any of the Turbostream URLs that we mentioned earlier.
Another popular distribution method is through app bundling. This is usually the case when you download freeware or those small apps that are free to use. Popular examples of freeware include file converters, file downloaders, torrent clients, file managers, system cleaners, free templates, and other free utilities. Don’t you ever wonder how they make money? They get paid by third parties to include the malicious app in their installer package.
When you install the freeware on your computer, you’re usually given two options: Quick install or Custom Install. Most users don’t want the hassle of going through everything just to install an mp3 converter or a YouTube downloader, so they often choose the Quick Install option. What they do not know is that the Quick Install process includes the automatic installation of the bundled malware. If you choose the Custom Install, you’ll be able to see every step of the installation process, including the malware’s attempt to install itself together with the app you downloaded.
Aside from bundling and sponsored ads, Turbostream is also distributed via phishing. Scam emails with links to Turbostream are often disguised as invoice emails, security alerts, software updates, or other types of phishing emails. When you click on the link, you will be directly sent to the Turbostream website.
What Does Turbostream Do?
When you visit any of the Turbostream websites, the first thing you see is a page that looks like a streaming website, complete with a fake media player. But all of these are fake. The media player is not even showing anything and just looks like a black box. Before you can do anything on the website, a message will pop up, asking you to allow the notifications on the website so that you can continue streaming. But whatever option you choose, the adware will still be downloaded on your website. You’ll then be redirected to various websites while showing lots of advertisements.
Here are some of the indications that your computer has been infiltrated by the Turbostream malware:
- Your web browser’s homepage has been inexplicably changed without your approval. If you check the new homepage, you’ll find that the URL is one of the Turbostream websites listed above.
- Advertisements appear frequently. The ads are no longer limited to the Turbostream website, but on other websites as well. In worse instances, the ads appear even when the browser is closed.
- When you click on links on other websites, you will be redirected to websites that are different from what you anticipated. This is because Turbostream turns normal words and phrases into hyperlinks and links them to their ads. So what you see are not actually links, but ads delivered by the malware.
- Some websites that you usually visit may not load properly because of the adware. This is because the malware messes with the layout of the webpages, as well as the content.
- Other apps are mysteriously installed on your computer.
Browser redirects and the presence of intrusive ads are the most common telltale signs of adware infection. Some adware may also come with a potentially unwanted program (PUP) that aids in the operation of the malicious software. Aside from these functions, most adware apps collect the victim’s personal information, such as browsing history, search queries, purchasing behavior, and other data that will help them deliver more targeted advertisements.
But what makes Turbostream risky is when it redirects you to external websites that might host dangerous malware, including ransomware and Trojans.
How to Remove Turbostream
Turbostream adware may be less dangerous compared to other malware types, but you still need to remove it from your computer as soon as possible. Even if you can stand the annoying ads, you have to consider the danger posed by the redirects and the data collection being undertaken by Turbostream.
However, getting rid of the Turbostream is easier said than done. You have to make sure that all components are deleted to make sure that it doesn’t come back. If you want to remove this adware from your computer, you need to follow our Turbostream removal instructions below:
Step 1: Quit All Turbostream Processes.
The first thing you need to do is to kill all processes associated with the adware. If you just try to uninstall the PUP or change back your browser’s default, you won’t be able to do it successfully and the changes will not be implemented. You need to quit all Turbostream processes via Task Manager by following the instructions below:
- Right-click on any empty part of the Taskbar, then choose Task Manager from the right-click menu.
- Under the Processes tab, look for any entry with Turbostream in the name.
- Click on the suspicious process, then click the End Process button.
- Do the steps above for all suspicious processes in Task Manager.
Step 2: Uninstall the Turbostream PUP.
If the adware came with a potentially unwanted program, or if you noticed some apps that were mysteriously installed on your computer, you need to uninstall them from your computer. To do this, just go to Setting > Apps > Apps & features, then look for the PUP or suspicious apps. Click Uninstall to remove it from your device. Continue with uninstalling the apps until all of the suspicious apps have been uninstalled.
Step 3: Scan For Leftover Files.
Once you have uninstalled the apps, use your anti-malware program to scan your computer for all infected files and delete them from your computer. Make it a habit to run a scan on a regular basis to make sure no malware gets past your security.
Step 4: Undo the Changes to Your Browser.
The next step is to finally revert the changes that the adware has done to your browser. You need to check your Firefox, Chrome, Internet Explorer, or Safari browser for any changes made by the adware and follow the steps below to undo them.
Here are the steps on how to undo the changes on Chrome:
Adware For Mac
- Uninstall the Turbostream extension by going to menu > More Tools > Extensions. Click the Remove button on the extension that you want to uninstall.
- Go to menu > Settings > Search engine, then set the default search engine by clicking the dropdown beside Search engine used in the address bar.
- Click Appearance on the left menu, then set the New Tab page and Homepage.
- If you prefer to reset everything, Click Advanced and scroll down to the Reset settings section. Click on Restore settings to their original defaults > Reset settings.
The steps are basically the same for the other browsers, except for some minor differences. All you need to do is go to the settings section and find the component you wish to edit.
Check Mac For Adware
Summary
Getting rid of the Turbostream adware can be a bit troublesome because you need to be thorough in the removal process. However, you’ll find that the process is less complicated when you follow our instructions above.